多机环境下虚机网络实现机制(二)
— VLAN和VXLAN流表实现机制
1、neutron中的网络概念
1.1 网络的命名空间
在 neutron中,网络名字空间可以被认为是隔离的拥有单独网络栈(网卡、路由转发表、iptables)的环境,只有拥有同样网络名字空间的设备,才能看到彼此。namespace的好处就是可以隔离网络设备和服务,在neutron中,使用ip netns来列举出所有的命名空间。
1 2 3 4 | |
以qdhcp开头的是DHCP服务的命名空间,以qrouter开头的是路由器服务的命名空间。 为了方便的使用namespace,可以使用ip netns exec namespaceID commond来对命名空间进行操作,如下所示:
1 2 3 4 5 6 7 | |
1.2 Security Group的概念
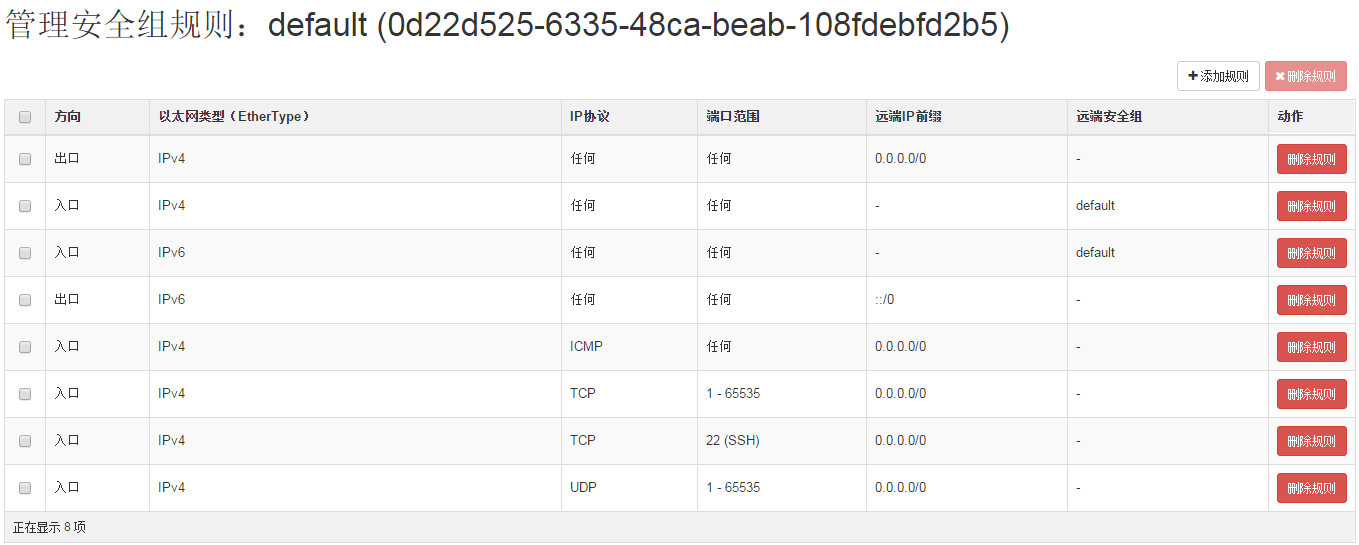
Security group是一些规则的集合,用来对虚拟机的访问流量进行控制,起到虚拟防火墙的作用,在启动虚拟机的实例时,可以将一个或者多个安全组与该实例关联,在nova中默认的存在一个default的安全组,可以在里面添加相应的规则。
在具体的实现上,底层使用的iptables,由于OVS并不支持iptables规则的tap设备,所以在compute节点使用Linux bridge进行实现。
要查看相应的安全组的规则,需要在compute节点上进行查看有三种方式,INPUT(进入),OUTPUT(出去)和FORWARD(转发)。 以INPUT为例,安全组是对应的bridge来说的,为了区分不同的安全组,可以通过查找vm上的tap设备来找到对应的安全组规则,这样就可以实现不同虚机和不同规则的安全组连接。 下面来查找INPUT的iptables规则,可以看到和安全组相关的规则都被重定向到neutron-openvswi-INPUT。
1 2 3 4 5 6 7 8 | |
继续查看neutron-openvswi-INPUT的iptables规则表,可以看到几个不同的tap设备对应着不同的neutron-openvswi规则,这主要是因为在该计算节点已经创建了几台不同的虚拟,而这tap设备就是与虚机的bridge所对应。
1 2 3 4 5 6 7 | |
在network01网络创建的host01的hostnameID为11f1d000-615b-4cee-b760-baef886b6637,那么找到所对应的tap设备后,找出其iptables的规则,如下所示
1 2 | |
可以看出规则被重定向都neutron-openvswi-oa1c05cb3-9,接着查看neutron-openvswi-oa1c05cb3-9的iptables规则,可以看到从虚机发送到DHCP的请求直接通过,而其他的请求则会转到neutron-openvswi-sa1c05cb3-9。
1 2 3 4 5 6 7 8 9 10 | |
接着查看neutron-openvswi-sa1c05cb3-9的规则,这条chain主要检查从vm发出来的网包,是否是openstack所分配的IP和MAC,如果不匹配,则禁止通过。这将防止利用vm上进行一些伪装地址的攻击。
OUTPUT和FORWARD的规则查看方法和INPUT的类似,可以依据上述方法进行安全组的学习
2、计算节点的流量转发机制
2.1 网桥介绍
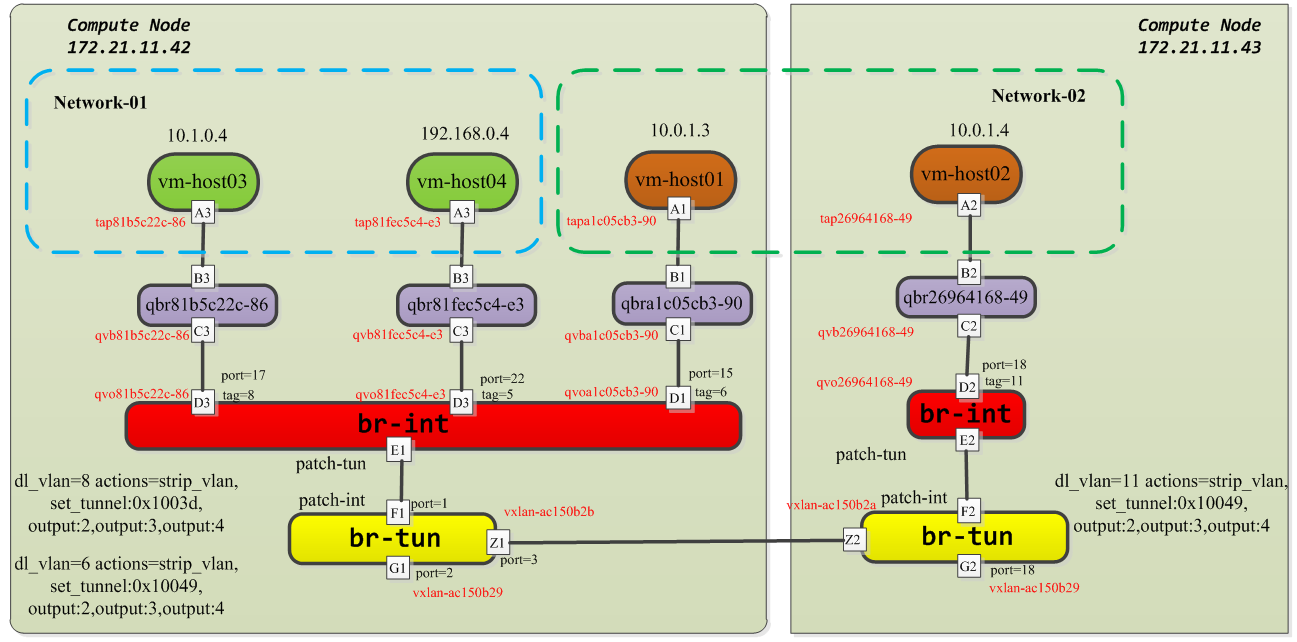
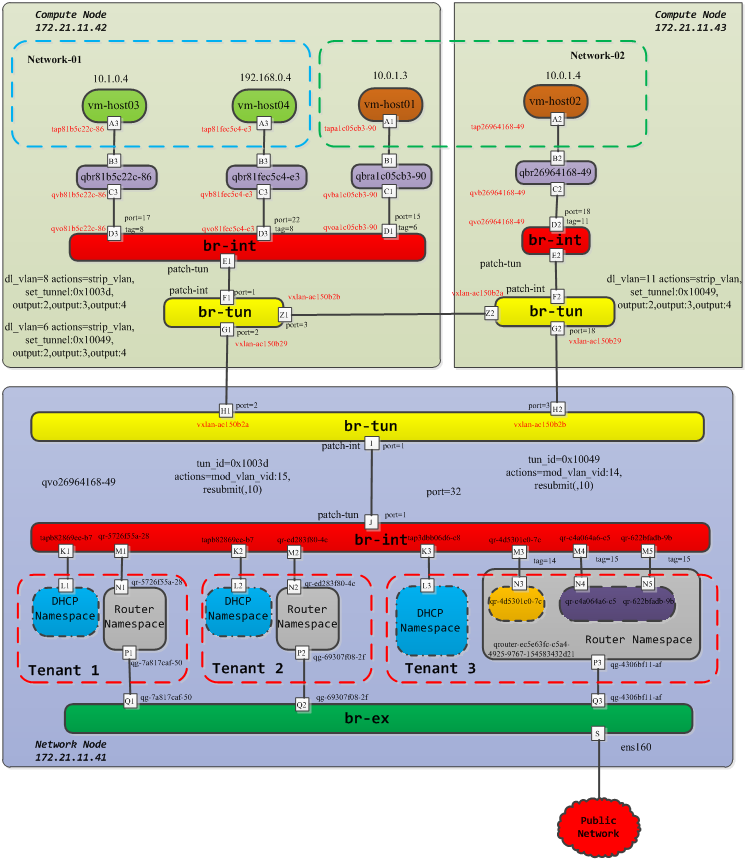
在多机环境下,分别在两个计算节点上部署虚机,网桥整体组成如下所示:
在compute节点上主要有两种网桥,一种是linux bridge,另外一种就是OVS网桥。
(1)linux网桥
主要用来绑定security group的iptables规则,与实际的转发并没有直接的关系,具体查看语法如下:
1 2 3 4 5 6 7 8 9 10 11 | |
(2)OVS网桥
在compute节点上主要包括两种,br-int和br-tun,br-int主要进行vlan标签的设置和转发,而br-tun主要用于vxlan标签的设置和转发流量。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 | |
2.2 Vlan标签设置以及流表转发机制
在ovs中,通过网桥br-int来对vlan和mac进行转发,主要是作为一个二层交换机使用,所包含的接口主要包括两类: - linux bridge过来的qvo-xxx - 往外的 patch-tun 接口,连接到 br-tun 网桥
这样就可以通过qvo-xxx 接口上为每个经过的网络分配一个内部 vlan的tag,如果在同一个neutron网络里启动了多台虚机,那么它们的tag都是一样的,如果是在不同的网络,那么vlan tag就会不一样。在多机环境中,分别在网络10.0.1.0/24和10.1.0.0/24里创建了两台虚机host01和host03,那么对应的tag分别为6和8。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | |
接着查看两台虚机所在网络的端口号,可以看到对应的port number分别为15和17,查看端口号主要为了方便读取流表的转换规则。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 | |
知道各自的port number后,对br-int的流表进行查看,找到port=15和port=17的流表规则如下所示:
1 2 3 4 5 6 7 8 9 | |
先根据priority的优先级找到table=0的flow规则,不管是ARP还是icmp都交给table=24来进行处理。
- vm发出ARP报文 : 以host01的虚拟网络为例,flow entry遇到从15口进入的arp,并且arp来源(arp_spa)是10.0.1.3的,让数据包通过(normal)。
1 2 | |
- vm发出ICMP报文 以host01的虚拟网络为例,flow entry遇到从15口进入的,目标地址为fe80::f816:3eff:fe1e:125e的icmp包就可以通过。
1 2 | |
2.2 Vxlan标签设置以及流表转发机制
neutron中的vxlan的设置规则相对来说就更加复杂一些,主要利用br-tun网桥来实现,该网桥主要根据自身的规则将合适的网包经过 VXLAN 隧道送出去,可以从两个维度来进行思考:
- 从vm内部过来的数据包进行规则的设置,数据包带着正确的vlan tag过来,从正确的tunnel扔出去;
- 数据包从外面public network带着正确的vxlan tunnel号过来,要修改到对应的内部的vlan tag扔到里面去。
以该多机环境为例,考虑创建的虚拟机在不同的计算节点,由于host01和host02分别创建在节点172.21.11.42和节点172.21.11.43上,所以会有不同的vxlan tunnelID,以host01所在的172.21.11.42的compute节点为例,查看br-tun网桥的信息。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | |
vxlan-ac150b29就是计算节点(42)和控制节点(41)在发送数据包时候的vxlan tunnel端口,patch-int端口主要连通br-int上的patch-tun端口。 下面来具体查看br-tun的流表规则:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | |
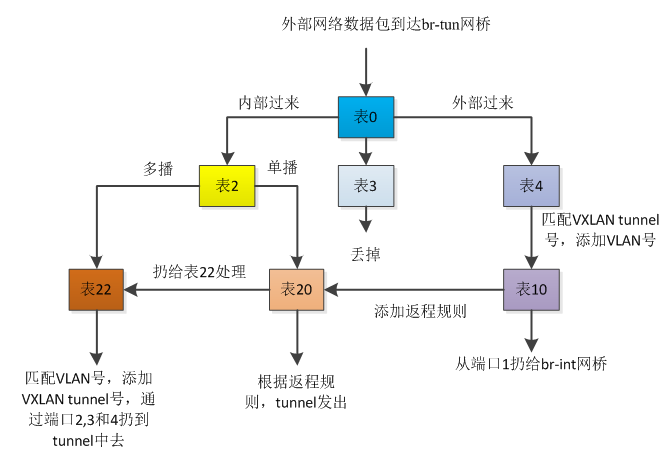
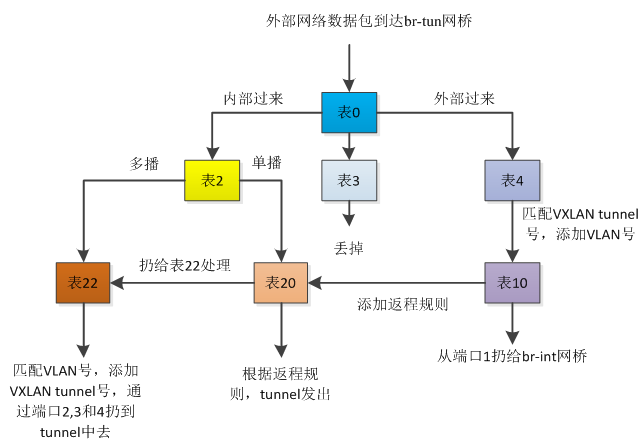
虽然表面上比较复杂,先要明确数据包出口的方向,由于在br-tun上存在两个方向的数据包转发,从内部vm过来的还有外部过来的,在该compute节点(172.21.11.42)上,br-tun的port值为1的端口表示从内部过来的数据包转发,port值为2表示数据包从外部进来的,port值为3表示数据包是从另外一个compute节点上的vm过来的。
上述的转发逻辑可以归结如下所示:
table=0
主要关注in_port=1,2和3的流表规则,从 1 端口(patch-int)进来的内部vm的网络包,扔给表 2 处理,从 2 端口(vxlan-ac150b29)外面进来的网包,扔给表 4 处理,从3端口(vxlan-ac150b2b)另外一个compute节点进来的数据包,扔给表4处理,其他的做drop处理。
1 2 3 4 5 | |
table=2
从里面vm出来的单播数据包扔给表20处理,多播和广播的数据包交给表22处理。
1 2 | |
table=3
经过表3处理的数据包全部扔掉
1
| |
table=4
主要处理外部过来的数据包,这里包括网络节点来的数据包以及其他compute节点过来的数据包。
- 匹配vxlan tunnel号为0x1003a的数据包,添加vlan=2的tag,扔给表10进行学习,再扔给br-int
- 匹配vxlan tunnel号为0x10049的数据包,添加vlan=6的tag,扔给表10进行学习,再扔给br-int
- 匹配vxlan tunnel号为0x1003d的数据包,添加vlan=8的tag,扔给表10进行学习,再扔给br-int
- 其它不匹配的直接扔掉
1 2 3 4 | |
table=6
经过表6的数据包直接扔掉处理。
1
| |
table=10
表10的作用是用来学习network节点或者其它compute节点过来的外部数据包,主要是vxlan tunnel进来的包,学习结束后往表20中添加对返程包的正常转发规则,然后扔给br-int。
table=20 说明是修改表 20 中的规则,后面是添加的规则内容;
- NXM_OF_VLAN_TCI[0..11],匹配跟当前流同样的 VLAN 头,其中 NXM 是 Nicira Extensible Match 的缩写;
- NXM_OF_ETH_DST[]=NXM_OF_ETH_SRC[],包的目的 mac 跟当前流的源 mac 匹配;
- load:0->NXM_OF_VLAN_TCI[],将 vlan 号改为 0;
- load:NXM_NX_TUN_ID[]->NXM_NX_TUN_ID[],将 tunnel 号修改为当前的 tunnel 号;
- output:NXM_OF_IN_PORT[],从当前入口发出。
1
| |
table=20
将数据包直接交给表22处理
1
| |
table=22
- 对于vlan tag=2的数据包,去掉valn tag,添加vxlan tunnel号为0x1003a,扔给端口2,3,和4
- 对于vlan tag=6的数据包,去掉valn tag,添加vxlan tunnel号为0x10049,扔给端口2,3,和4
- 对于vlan tag=8的数据包,去掉valn tag,添加vxlan tunnel号为0x1003d,扔给端口2,3,和4
- 其它不匹配的就直接丢掉
1 2 3 4 | |
3、网络节点的Vxlan流量转发机制
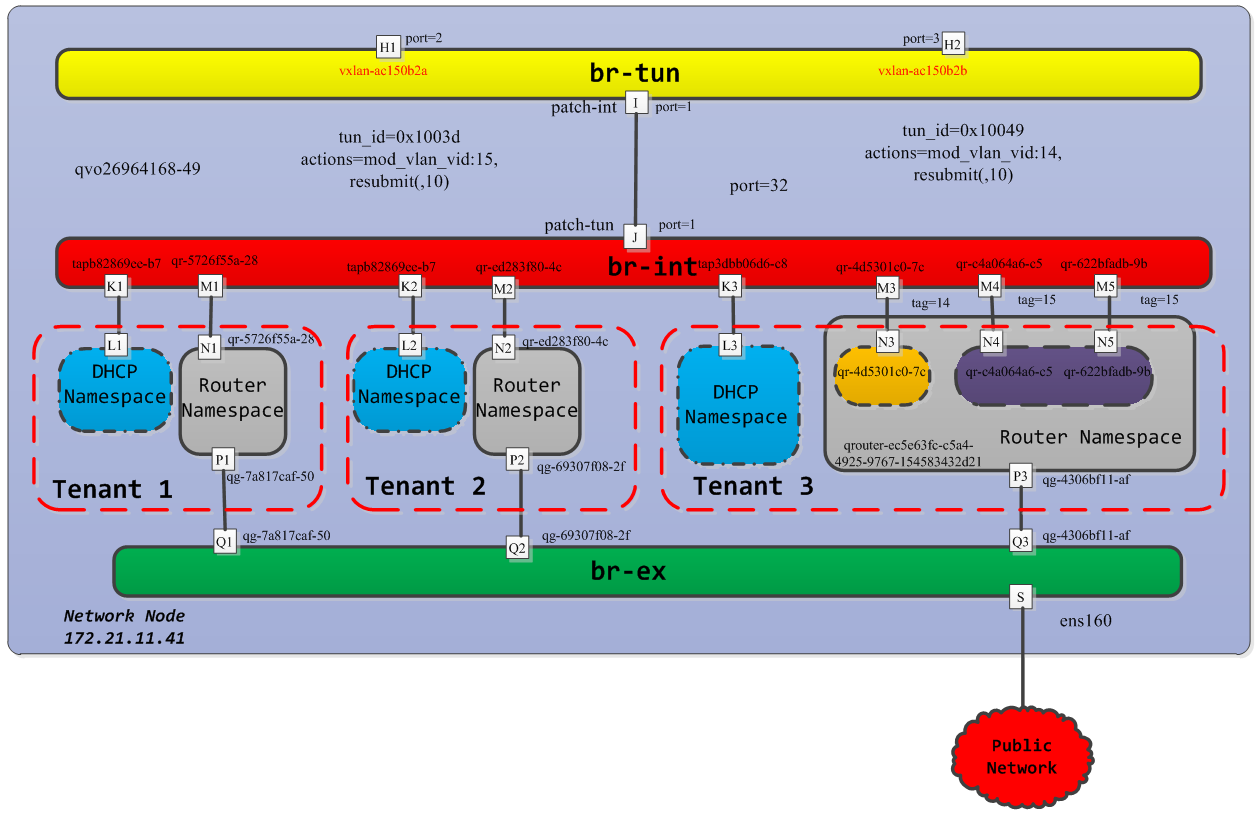
多机环境下,网络节点的网桥整体结构如下所示:
在该多机环境下,网络节点和控制节点部署在一起,网络节点所部署的neutron服务,包括DHCP服务和路由服务等。 该controller节点主要包括三种类型的网桥,br-int,br-tun,br-ex。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 | |
3.1 vxlan标签设置以及流表转发机制
类似于计算节点的VXLAN tunnel,network节点的VXALN规则也是通过br-tun网桥来实现的,该网桥主要根据自身的规则将合适的网包经过 VXLAN 隧道送出去,可以从两个维度来进行思考:
- 从vm内部过来的数据包进行规则的设置,数据包带着正确的vlan tag过来,从正确的tunnel扔出去;
- 数据包从外面public network带着正确的vxlan tunnel号过来,要修改到对应的内部的vlan tag扔到里面去。
以多机环境中172.21.11.41上的network节点为例,查看br-tun网桥的信息。可以看到不同的VXLAN tunnel号对应不同的网络连接。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | |
下面来具体分析br-tun网桥上的流表信息,分析方法和之前计算节点上的br-tun网桥基本一致,具体流表信息如下所示:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 | |
将上述的流表规则进行整理可以得到:
3.2 VLAN标签设置以及流表转发机制
在network节点上,vlan tag的设置主要在br-int网桥上进行,作为一个正常的二层交换设备进行使用,只是根据vlan和mac进行数据包的转发。接口类型包括:
- tap-xxx,连接到网络 DHCP 服务的命名空间;
- qr-xxx,连接到路由服务的命名空间;
- patch-tun 接口,连接到 br-tun 网桥。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 | |
转发流表也比较简单,表0中进行正常的转发,其他的就直接丢弃。
1 2 3 4 5 6 | |
3.3 和外部网络通信实现机制
主要通过br-ex网桥和public network进行通信, 一个是挂载的物理接口上,如 ens160,网包将从这个接口发送到外部网络上。 另外一个是 qg-xxx 这样的接口,是连接到 router 服务的网络名字空间中,里面绑定一个路由器的外部 IP,作为 nAT 时候的地址,另外,网络中的 floating IP 也放在这个网络名字空间中。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | |
查看流表规则,基本就是正常的转发动作。
1 2 3 4 | |
3.4 DHCP服务实现机制
dhcp服务是通过dnsmasq进程(轻量级服务器,可以提供dns、dhcp、tftp等服务)来实现的,该进程绑定到dhcp名字空间中的br-int的接口上。可以查看相关的进程。
3.5 路由服务实现机制
neutron中的路由服务主要是提供跨子网间的网络通信,包括虚拟想访问外部网络等。路由服务主要利用namespace实现不同网络之间的隔离性。另外,router还可以实现tenant network和external network之间的网络连接,通过SNAT实现tenant network往external network的网络连通性(fixed IP),通过DNAT实现external network往tenant network的网络连通性(floating IP),
1 2 3 4 | |
在该network节点上创建的路由服务是qrouter-ec5e63fc-c5a4-4925-9767-154583432d21,于是可以进一步查看namespace中的信息。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 | |
其中,qg-4306bf11-af是连接br-ex网桥的端口,负责外面的数据包的转发和处理,qr-XXX用于连接br-int网桥,处理带有VLAN tag的网络包。
1 2 3 4 5 6 | |
从上面规则中可以看出,从三个不同的qr-XXX端口进来的数据包都会通过qg-4306bf11-af发送到br-ex中去,从而到达外网。
综上所述,在多机环境下,计算节点和网络节点的整体网桥连接以及VLAN和VXLAN实现原理如下所示: